Know Everything About IS Audit

IS Audit | 3.imimg.com
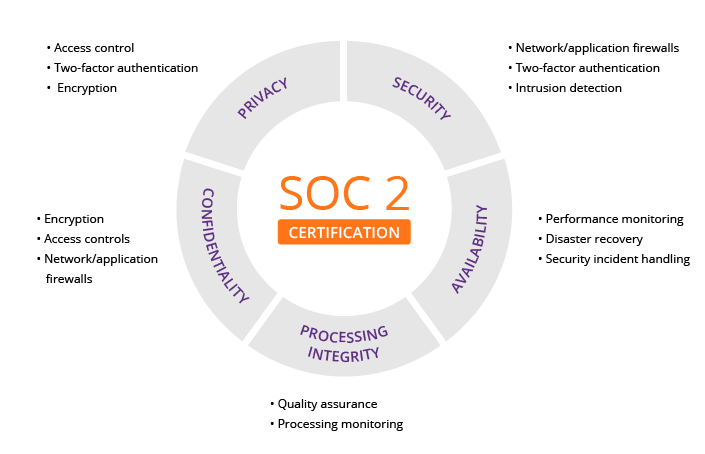
Unlike the financial audit, and information system audit is the process of evaluating the controls of information technology infrastructure of the whole organization or entity. The audit includes analysis of the information system, practices, assets, and operations of the organization. Furthermore, through Information system audit ensure and safeguards assets, preserves data integrity, and operating efficiently and competently to attain the goal and objective of an organization.
Why IS Audit Is Carried Out?
With an IS audit, the organization will be able to determining dangers that are related to IT assets, and in evaluatingcontrolsto decrease risks. Generally, IT audit is carried out in forms of “specific control review”. Information system audit is carried out to analyses company’s or entity’s confidentiality,availability, and integrity.
It also covers...